Physical security
Is made to give protection of personal data, hardware, software and networks from physical threats or technical threats such as hacking, malware and cyber attacks that could be the reason of loss or damage to an organisation.
Example: Physical Security and Cybersecurity Need to Converge, as networks evolved, security lost its way.
https://www.afcea.org/content/physical-security-and-cybersecurity-need-converge
Locks


This is a way of preventing unauthorised access to an establishment. Locks are installed to doors, windows, cabinets and important containers. There are two types of lock, the normal and modern. Normal locks are the metal locks that can be opened by a key. Where as, the modern locks are used barcodes as a verification method and can be opened by a key card.
Example: Burglars using blowtorches to break into homes in terrifying trend
https://www.thesun.co.uk/news/10285097/burglaries-blowtorch-uk-burglar-homes-locks/
Visitors passes

This is a system used in businesses to allow visitors to have a temporary access to the organisation. This is normally made like a card that must be worn by the visitor all the time. The modern version is a key card with a temporary and limited area access to the establishment. These passes are very important to the business world so that employers can identify or recognize their visitors and to also ensure that you will be able to enter the establishment.
Example: Keesler AFB changes ID requirements to get on base, that means all driver and passengers must now show a valid Department of Defense identification, or have a visitor’s pass to enter the installation.
https://www.wlox.com/2019/11/20/keesler-afb-changes-id-requirements-get-base/
Sign in/out systems

This system is used to be able to track the employers when they enter and leave the building. In this case they usually use a key card. This is very helpful because when someone lost his key card they can identify who and where they used it and they can also check the CCTV footage to check who is the culprit of the stolen key card.
Example: EntrySign makes signing visitors in and out quicker and easier
https://www.osbornetechnologies.co.uk/entrysign/
Biometrics

This is an authentication method. This is used to identify someone by checking their certain characteristics and traits.
Example: New vehicles with biometrics features coming as auto access control market grows
Retinal scans

This rely on unique physiological characteristics of the eye to identify an individual.
Example:Apple may take Face ID to the next level, scan retinas for increased security
https://www.digitaltrends.com/computing/apple-faceid-scan-retinas-security/
Fingerprint

It is a type of electronic security system that uses fingerprints for biometric authentication. This work by capturing the pattern of ridges and valleys on a finger.
Example:Hackers use a photograph of a fingerprint to bypass phone security
https://www.techradar.com/news/hackers-use-a-photograph-of-a-fingerprint-to-bypass-phone-security
Voice recognition

It is a program or hardware device with the ability to translate the human voice. Voice recognition is commonly used to run a device or perform different commands.
Example:Amaryllo launches biometric security camera with voice recognition
Guards

Security Guards duties includes securing buildings and personnel by patrolling the area, monitoring surveillance equipment and inspecting buildings and equipment. They can also have access points as well as allowing or prohibiting entry.
Example: German hospitals hire security guards after wave of violence
Cable shielding
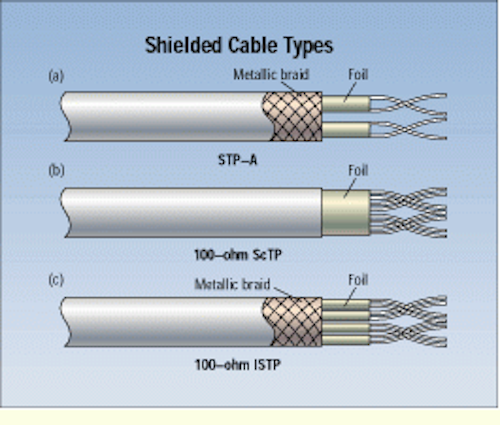
Shielded cables are used to protect the data being transferred through the cable from degradation by EMI exposure, which is common in data centers, industrial settings, offices, and other settings where computer technology, electrical equipment, or electronic equipment is in heavy use.
Example:Shielded Cable Primer
Software and network security

Software security is made to protect software against malicious attack and other hacker risks so that the software continues to function correctly. While, network security is made to prevent and protect against unauthorized intrusion into corporate networks.
Example: Make it So: How Intent-Based Network Security Accelerates the Enterprise
https://www.infosecurity-magazine.com/opinions/intent-network-security/
Encryption techniques

Encryption is the process of taking a readable plain text document or image and scrambling the texts to an extent that it is no longer understand. The intent of encryption is hide and protect the contents of that file from improper disclosure.
Public and private key

Public and Private key pair comprise of two uniquely made by long random numbers. Public key is made available to everyone via a publicly accessible directory. On the other hand, the private key must remain confidential to the owner.
Example: End-to-End Encryption, Next Tech Target
https://www.cloudwedge.com/news/end-to-end-encryption-next-tech-target/
Call back

A function that is move into another function as an argument, which is then bring up inside the outer function to complete different actions.
Example: Callback Functions
https://www.w3schools.com/jquery/jquery_callback.asp
Handshaking
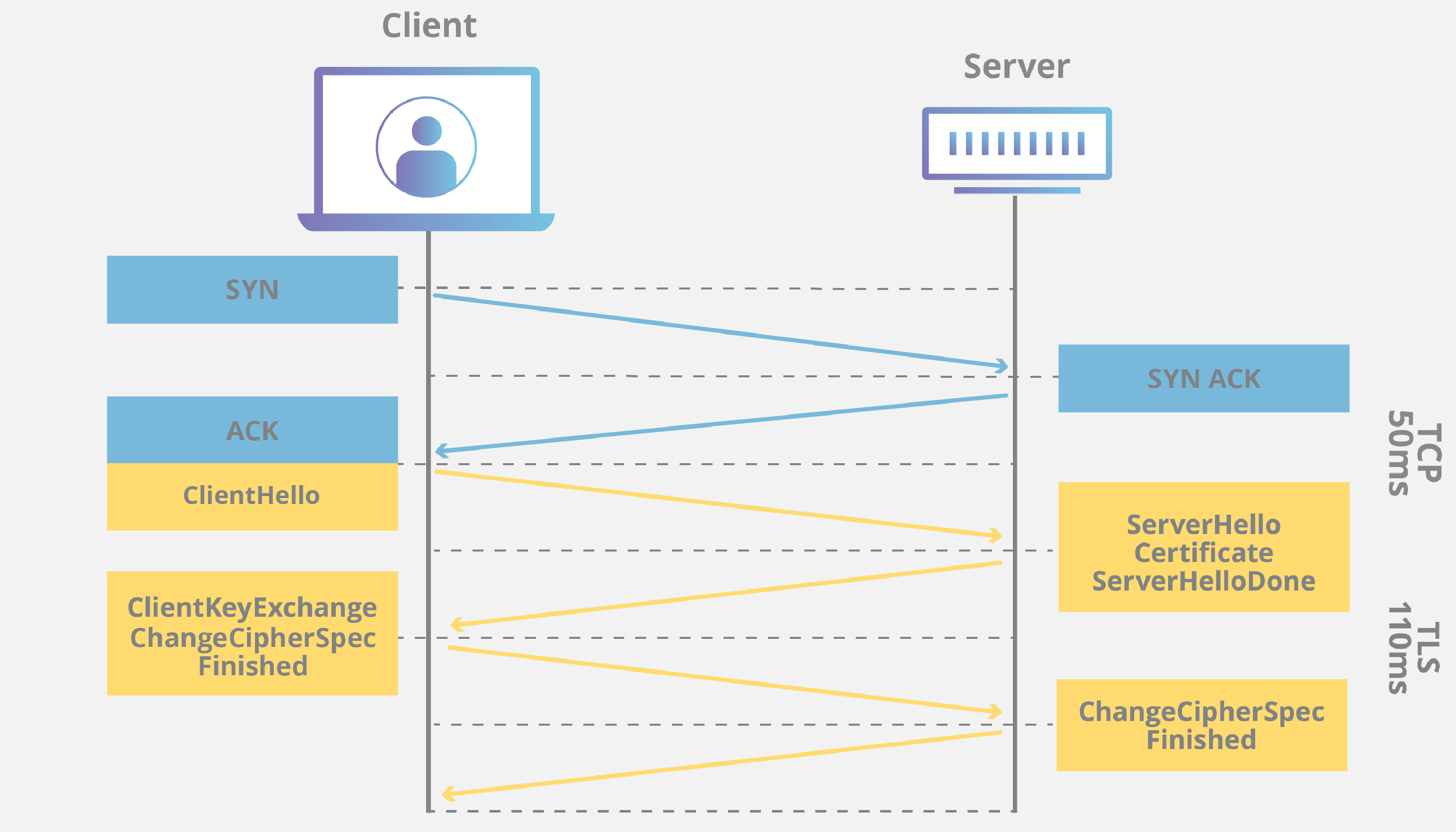
Two sides exchanging messages to acknowledge and verify each other, establish the encryption algorithms they will use, and agree on session keys.
Example:Man-in-the-Middle (MITM) Attacks
https://securityboulevard.com/2019/11/what-are-man-in-the-middle-mitm-attacks/
Diskless networks

A diskless network is a group of workstations that have no individual hard-drives and relies on a network boot from the server to boot an operating system on to each workstation.
Example:Thin Clients Booting over a Wireless Bridge
https://www.linuxjournal.com/article/9850
Use of backups
Backup refers to the process of making copies of data or data files to use in the event the original data or data files are lost or destroyed.
Example:Android Users Experience Failed Google Drive Backups For Months
https://www.gizmodo.co.uk/2019/11/android-users-experience-failed-google-drive-backups-for-months/
Audit logs

This is used to examine what activities have occurred on the system and are typically used for diagnostic performance and error correction. This helps to maintain system stability to workers.
Example:Over 21,000 organisations that use Oracle’s E-Business Suite could be at risk of financial fraud or theft as hackers can exploit a number of critical vulnerabilities known as PAYDAY to hijack an Oracle EBS system, reroute invoice payments, and erase audit logs to cover up their activity.
https://www.teiss.co.uk/payday-flaws-oracle-e-business-suite/
Firewall configuration

A firewall is a tool in security that is used in networks for preventing malicious attacks. It needs to be configured in order for it will not give the correct use.
Example: How firewall automation can help prevent breaches caused by wrong configurations
Virus checking software

These are programs that are developed to protect computers from malware like viruses, computer worms, spyware, etc. Their functions are also to scan, detect and remove viruses the computer.
Example:How We Test Antivirus and Security Software
https://uk.pcmag.com/security-software/84684/how-we-test-antivirus-and-security-software
Use of virtual private networks (VPN)

A VPN, or virtual private network, is a secure transmission between two or more devices. VPNs are used to protect private web traffic from snooping, interference, and censorship.
Example:NordVPN Lists Five Measures to Bolster Its Security, Keyfactor’s CTO, Ted Shorter, Shares His Views
Intruder detection systems

A device that checks a network for malicious activity or policy violations. Any malicious activity or violation is typically reported or collected centrally using a security information and event management system.
Example:Global Perimeter Intrusion Detection Systems Market Growth Will Escalate Rapidly 2019-2026 by Global Top Brands United Technologies, Harper Chalice Group Ltd., Godrej.com, Senstar Corporation, Future Fiber Technologies
Passwords

These are made to ensure the security and confidentiality of data that is stored on workstations and servers.
Example:How to manage your password like a boss, well, CISO
https://www.itproportal.com/features/how-to-manage-your-password-like-a-boss-well-ciso/
Levels of access of data
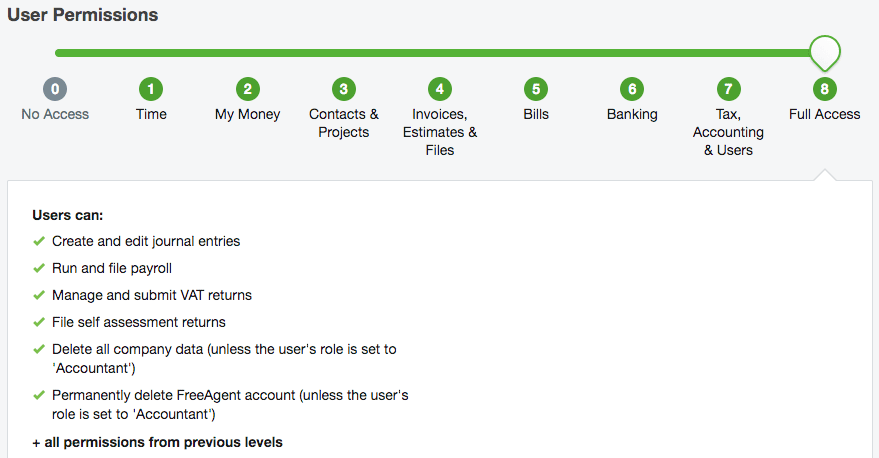
Different levels of access is made to help to ensure that the network remains secure and that only licensed software is used on it.
Example:Database management systems
https://www.bbc.co.uk/bitesize/guides/zb2hgk7/revision/4
Software updating

Software updates usually contains improvements which are helpful in the system as they also have patches to cover security vulnerabilities which are found along with issues.
Example:Windows 10 November 2019 Update common problems and how to fix them
https://www.windowscentral.com/windows-10-november-2019-update-common-problems-and-how-fix-them
Disaster recovery

Its work is to provide the procedures that prepare an organization’s especially the IT infrastructure to effectively recover from natural or human-induced disasters like cyber attacks and equipment failure and to ensure business continuity.
Example: Michael Spletto Joins Tetra Tech’s Disaster Recovery Practice
Backup systems

Holding the same copies of the data enables the failing system to be able to switch to an alternate system. The reason is, possessing different backup systems, with multiple copies of the data which leads to extra systems, allows you to distribute across multiple different systems in a network.
Example: Backup Software That Saves Your Servers From Ruin
Whole system replacement
If this occurs it means you have experienced a disaster of unforeseen proportions. Many businesses will have a contract named “dark site” who, when the system fails, will be hired to duplicate the businesses system.
Example:Vertebral Body Replacement System Market Poised for Excellent Growth During (2019-2026)
Tiers of recovery

Tier 0: No off site data, this is where the data is unsafe. If there is a power surge this will be the end of all the companies data.
Tier 1: Data backup with no “dark site”. This is where the backups are taken, but there is no replacement location if the system fails.
Tier 2: Data backup with a “dark site”. This is where the copies of the data are taken, but there is a centre available to transfer data control to.
Tier 3: Electronic vaulting. Mirrored copies of the system are continuously maintained.
Tier 4: Point-in-time copies. Remote copies of the data are the same as local data.
Tier 5: Transaction integrity. The system ensures both copies are in tune with each other.
Tier 6: Zero or near-Zero data loss. For very fast systems, where a sudden fault, could result in some minor transnational data loss
Tier 7: Highly automated, business-integrated solution. Now the system will do all the thinking for you.
Example:SME disaster recovery made easy with cloud, hybrid and HCI
https://www.computerweekly.com/feature/SME-disaster-recovery-made-easy-with-cloud-hybrid-and-HCI